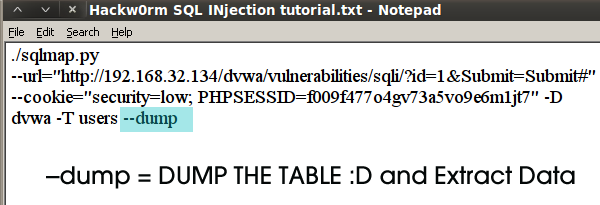
Steps
- 1
1
Open the site you want to hack. Provide wrong username/password combination in its log in form. (e.g. : Username : me and Password: ' or 1=1 --)An error will occur saying wrong username-password. Now be prepared your experiment starts from here.
2
2
Right click anywhere on that error page =>> go to view source.
3
There you can see the HTML coding with JavaScript.• There you find somewhat like this....<_form action="...Login....">• Before this login information copy the URL of the site in which you are. (e.g. :"< _form..........action=http://www.targetwebsite.com/login.......>")
4
Then delete the JavaScript from the above that validates your information in the server.(Do this very carefully, your success to hack the site depends upon this i.e. how efficiently you delete the java scripts that validate your account information)
5
Then take a close look for "<_input name="password" type="password">"[without quotes] -> replace "<_type=text> “there instead of "<_type=password>". See there if maximum length of password is less than 11 then increase it to 11 (e.g. : if then write )
6
Just go to file => save as and save it anywhere in your hard disk with ext.html(e.g.: c:\chan.html)
7
Reopen your target web page by double clicking 'chan.html' file that you saved in your hard disk earlier.• You see that some changes in current page as compared to original One. Don't worry.
8
Provide any username [e.g.: hacker] and password [e.g.:' or 1=1 --] You have successfully cracked the above website and entered into the account of List user saved in the server's database.
Warnings
- Do the coding and changes very carefully, your success to hack the site depends upon this i.e. how efficiently you delete the java scripts that validate your account information.
- You are not logged in so your IP address will be recorded in this page's edit history. You may loginor create an account.
- == Warnings ==
- *Do the coding and changes very carefully, your success to hack the site depends upon this i.e. how efficiently you delete the java scripts that validate your account information.
- [[es:hackear una página web con HTML]]
- [[pt:Hackear um Site com Códigos Básicos em HTML]]
- [[it:Violare un Sito Web Utilizzando Codice Html]]
- [[de:Eine Webseite mit einfachem HTML hacken]]
- [[fr:pirater un site Internet avec du HTML]]
- [[nl:een website hacken met simpele HTML code]]
- wikiHow is a collaborative writing project. You should expect other wikiHow community members will edit and build upon the writing that you submit here. By submitting your writing, you confirm that you wrote this content or have received permission from the copyright holder to post it here. In addition, you agree to our Terms of Use, and are willing to have your work released under a Creative Commons License.
12:58 |
Category: |
266
comments









.jpg)
.png)
.png)

.png)

.png)
.png)
.png)


+(1).png)